Tuesdays massive ransomware outbreak was, in fact, something much worse [View all]
https://arstechnica.com/security/2017/06/petya-outbreak-was-a-chaos-sowing-wiper-not-profit-seeking-ransomware/
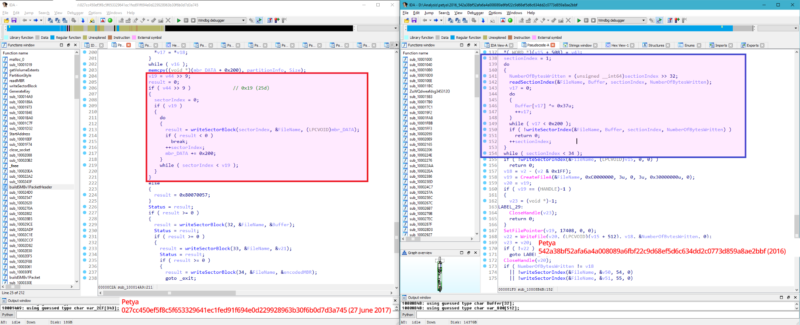
Code in Tuesday's attack, shown on the left, was altered to permanently destroy hard drives.
QUOTE
Initially, researchers said the malware was a new version of the Petya ransomware that first struck in early 2016. Later, researchers said it was a new, never-before-seen ransomware package that mimicked some of Petya's behaviors. With more time to analyze the malware, researchers on Wednesday are highlighting some curious behavior for a piece of malware that was nearly perfect in almost all other respects: its code is so aggressive that it's impossible for victims to recover their data.
In other words, the researchers said, the payload delivered in Tuesday's outbreak wasn't ransomware at all. Instead, its true objective was to permanently wipe as many hard drives as possible on infected networks, in much the way the Shamoon disk wiper left a wake of destruction in Saudi Arabia. Some researchers have said Shamoon is likely the work of developers sponsored by an as-yet unidentified country. Researchers analyzing Tuesday's malware—alternatively dubbed PetyaWrap, NotPetya, and ExPetr—are speculating the ransom note left behind in Tuesday's attack was, in fact, a hoax intended to capitalize on media interest sparked by last month's massive WCry outbreak.
"The ransomware was a lure for the media," researcher Matt Suiche of Comae Technologies, wrote in a blog post published Wednesday. "This version of Petya actually wipes the first sectors of the disk like we have seen with malwares such as Shamoon." He went on to write: "We believe the ransomware was in fact a lure to control the media narrative, especially after the WannaCry incidents, to attract the attention on some mysterious hacker group rather than a national state attacker like we have seen in the past in cases that involved wipers such as Shamoon."
Suiche provided the above side-by-side code comparison contrasting Tuesday's payload with a Petya version from last year. Both pieces of code take aim at two small files—the master boot record and master file table—that are so crucial that a disk won't function if they are missing or corrupted. But while the earlier Petya encrypts the master boot record and saves the value for later decryption, Tuesday's payload, by contrast, was rewritten to overwrite the master boot record. This means that, even if victims obtain the decryption key, restoring their infected disks is impossible.
UNQUOTE
